Introduction
Nigeria is one of Africa’s largest economies, yet for over a decade, it has struggled to address devastating jihadi insurgencies and terrorism by Boko Haram, security in the North-eastern Nigeria has significantly deteriorating since 2017. Vulnerability Assessment to critical infrastructure has not been adequately addressed in the North East. Thus, the purpose of this paper is to identify the critical infrastructure and vulnerability assessment using GIS based approach.
Vulnerability is defined as the relationship between a facility’s desirability as a target and the level of deterrent and/or defense provided by existing countermeasures. The function and/or symbolic relevance of the facility determine target attractiveness, which is a measure of the asset or facility in the eyes of an attacker. Vulnerability means different things to different people and the term is often confused with risk. Buckel (2000) contends that work must be done to clear up the definition of vulnerability with respect to risk. For example, Emergency Management Australia (1998) defines vulnerability as the degree of susceptibility and resilience of the community and environment to hazards. Likewise, the Emergency Management Australia (1998) glossary of terms interchanges the terms vulnerability analysis with hazard analysis or vulnerability assessment. National Water Resources Association (NWRA) (2002) defines a vulnerability assessment as the identification of weaknesses in security, focusing on defined threats that could compromise its ability to provide a service. Blaike et al. (p. 4, 1994) defines vulnerability as “the characteristics of a person or group in terms of their capacity to anticipate, cope with, resist, and recover from the impact of a natural hazard”.
“Critical infrastructure” consists of systems and assets so vital to the whole community that their incapacity would harm the physical community security, economic security or public health. Critical infrastructure is often geographically concentrated, so it may be distinctly vulnerable to events like natural disasters, epidemics, and certain kinds of terrorist attacks. Throughout this research, the concept of vulnerability and processes for assessment in critical infrastructures due to a security threat. In order to investigate the vulnerability of a system and to get informative answers it is necessary to raise the questions: “Why is the system vulnerable?”, “What is it vulnerable to?”, “How vulnerable is it?” and “Where is the vulnerability located?” (Turner et al 2003). The answers provided can be useful for strengthening the resilience of a system and thus reducing the vulnerability (Semadeni-Davis et al 2007; Mossberg-Sonnek et al. 2007; Vogel et al. 2007; Adger 1999).
All facilities are exposed to a certain level of risk from a variety of threats. These dangers could arise as a result of natural disasters, accidents, or malicious activities. Regardless of the nature of the hazard, facility owners must restrict or manage the risks posed by these threats to the greatest extent practicable. The vulnerability assessment examines both the potential loss from a successful attack and the facility’s/vulnerability locations to an assault. The degree to which a successful attack from a given danger compromises the agency’s mission is known as the impact of loss. The accurate definition of the ratings for impact of loss and vulnerability is an important part of the vulnerability assessment. These definitions may differ significantly from one facility to the next. The length of time that mission capability is harmed, for example, is a significant factor in the impact of loss.
Critical infrastructure (CI) can be harmed in a variety of ways, including natural (e.g., flooding) and manmade (e.g., earthquakes) (e.g., accident, robbery, terrorist attack). Their impacts can range from little disruption to catastrophic catastrophe, depending on whether they affect infrastructure or, as a result of a domino effect, multiple other key sectors (Security and Forensic Sciences, 2016). Terrorist attacks involving explosive devices warrant special attention since they can occur in a variety of ways, and while another type of threat may emerge in the future, it has historically been one of the most regularly used techniques by terrorists. Critical infrastructure may include communications, emergency services, energy; dams, finance, food, public services, industry; health; transport; gas; public communications, radio and television, information technology, commercial facilities; chemical and nuclear sectors; and water. The use of Remote Sensing and GIS based approach for Vulnerability Assessment of Critical Infrastructure will expose areas in the Northeast that are lacking these critical infrastructures and also help in location where such infrastructures have been destroyed by insurgency, Terrorism. Certain types of terrorist attacks could be of sufficient scale to pose a geographic threat to critical infrastructure. Nuclear bombs, radiological weapons (“dirty” bombs), or electromagnetic pulse (EMP) devices could damage or render Inaccessible concentrated critical assets. Cyber-attacks on regional computer systems also have the potential to damage or disrupt computer networks’ ability to control critical infrastructure. Biological attacks could have impacts similar to those of epidemics, although they could be more specifically targeted at particular regions
Methodology
Determining what constitutes “critical infrastructure” is nearly as difficult as defining “terrorism” in a way that is universally acceptable, given the ramifications of including and excluding certain services and businesses.
The United States’ Presidential Policy Directive 21 (PPD-21): Critical Infrastructure Security and Resilience identified 16 critical infrastructure sectors whose “assets, systems, and networks, whether physical or virtual, are considered so vital to the country that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof,” according to the directive.
These are some of them:
- Health care and public health
- Government facilities
- Commercial facilities that draw large crowds of people for shopping, business, entertainment, or lodging.
- Information systems that include, the internet for example, (the system and protecting the physical network as well as mobile and fixed telecommunication and satellites, also needed for navigation).
- Transportation to include all possible forms of transportation from road, rail, air (airplanes and airports, as well as air traffic), sea, and inland waterway transport.
- Energy (e.g., oil, gas, wind turbines, solar farms) that is needed in the production of electricity, its storage and distribution
- National monuments that are important in representing a country’s national identity as well as religious institutions with references to churches, mosques, and synagogues. Symbolism in attacking these facilities and the emotional reaction following an attack make it a favourable target in hate crimes (targeting only the facility) to severe incidents of hate crimes and acts of terrorism.
- National monuments
- Food and agriculture aimed at the production and delivery of food suitable for human consumption.
- Financial services with reference to banking and payment services.
In this study, data processing and analysis procedures follow these four steps discussed in their sequential order of operation. The steps are:
- Acquisition of critical infrastructure datasets.
- Acquisition of Insurgency (Fatalities) Data sets
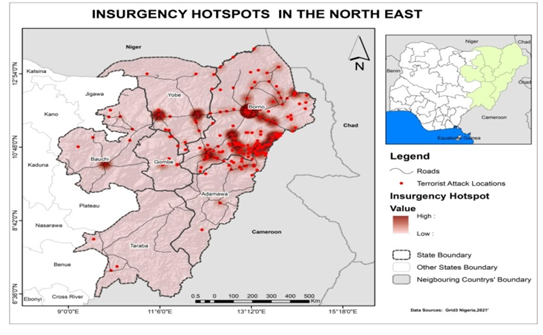
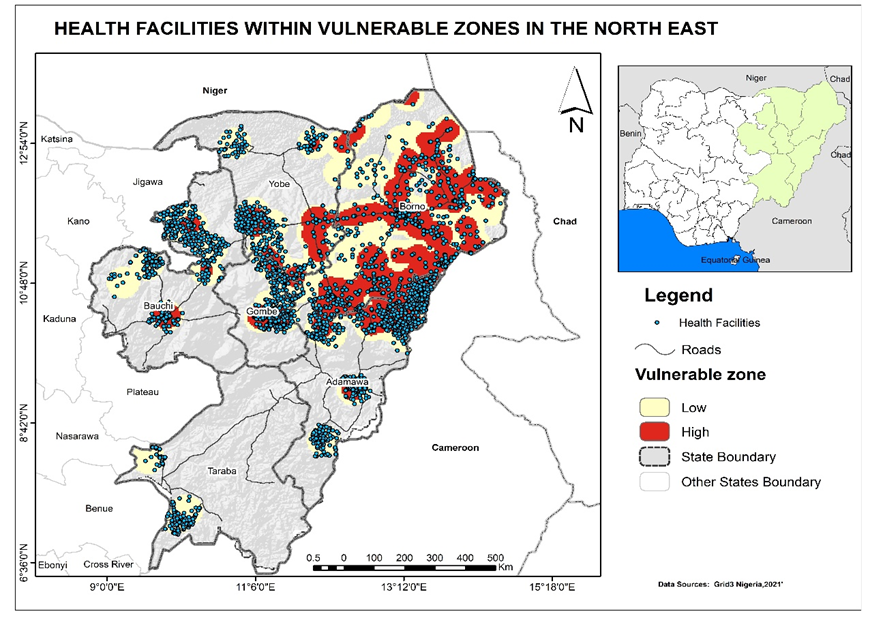
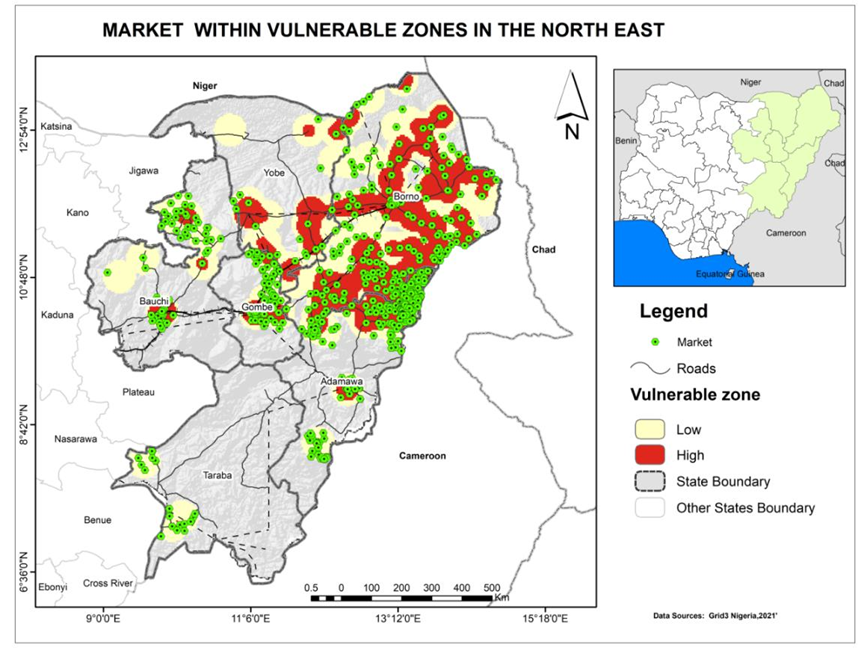
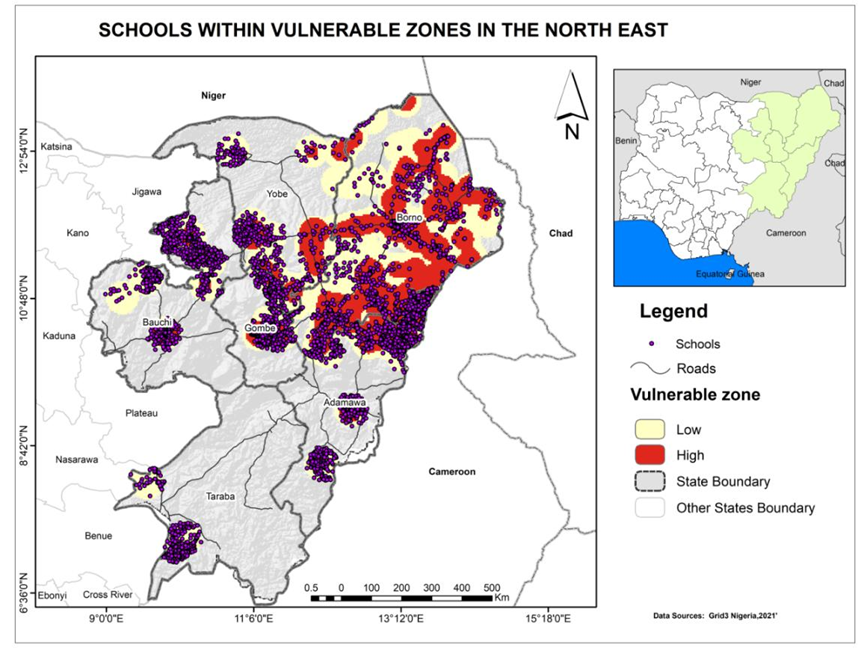
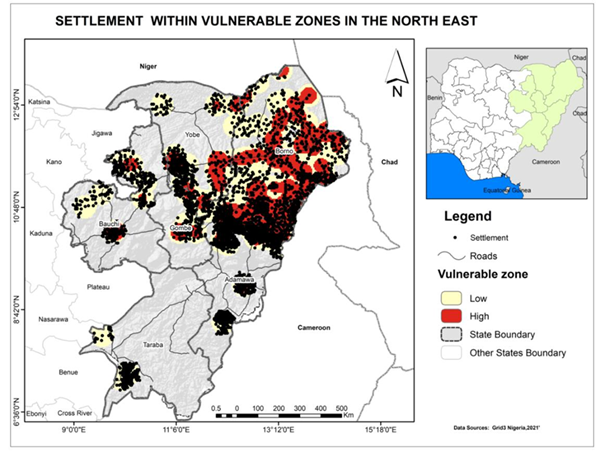
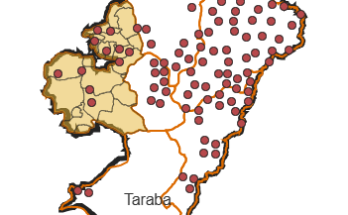
- Hotspots Analysis of vulnerable Zones of Critical Infrastructure
- Overlay Analysis of Critical Infrastructure on Vulnerable Zones
Results & Findings